Get Started
Quickstart
This page provides an overview of the main features available in Myrmex Cloud.
Most used resources
Navigation in Myrmex is designed to dynamically adapt to the user interface, providing a fluid and intuitive experience. Depending on the size of your navigation window, elements can automatically adjust to optimize usability and access to essential functionalities.Cybersecurity assistant
MYRMEX AI (Inteligência Artificial do Myrmex)
MYRMEX AI (Inteligência Artificial do Myrmex)
Request log collection and analysis;
View detected alerts;
Manage MYRMEX Agent Installation;
Create and manage users;
Monitor the health of the environment, among other functions.
Dashboard
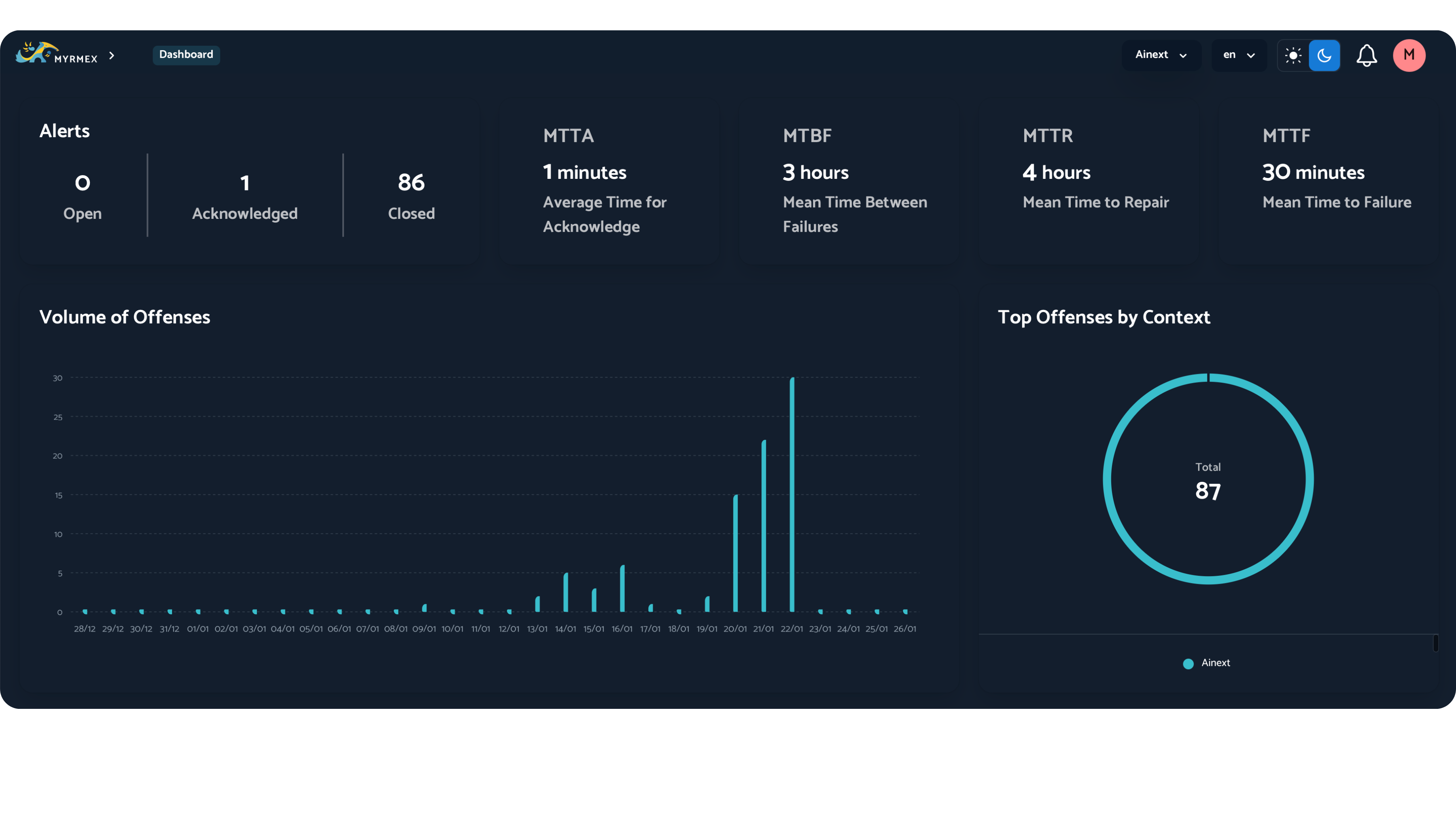
- Predefined dashboards for quick visualization of common data;
- Creation of customized dashboards with configurable graphs to meet the specific needs of your operation.
Environments
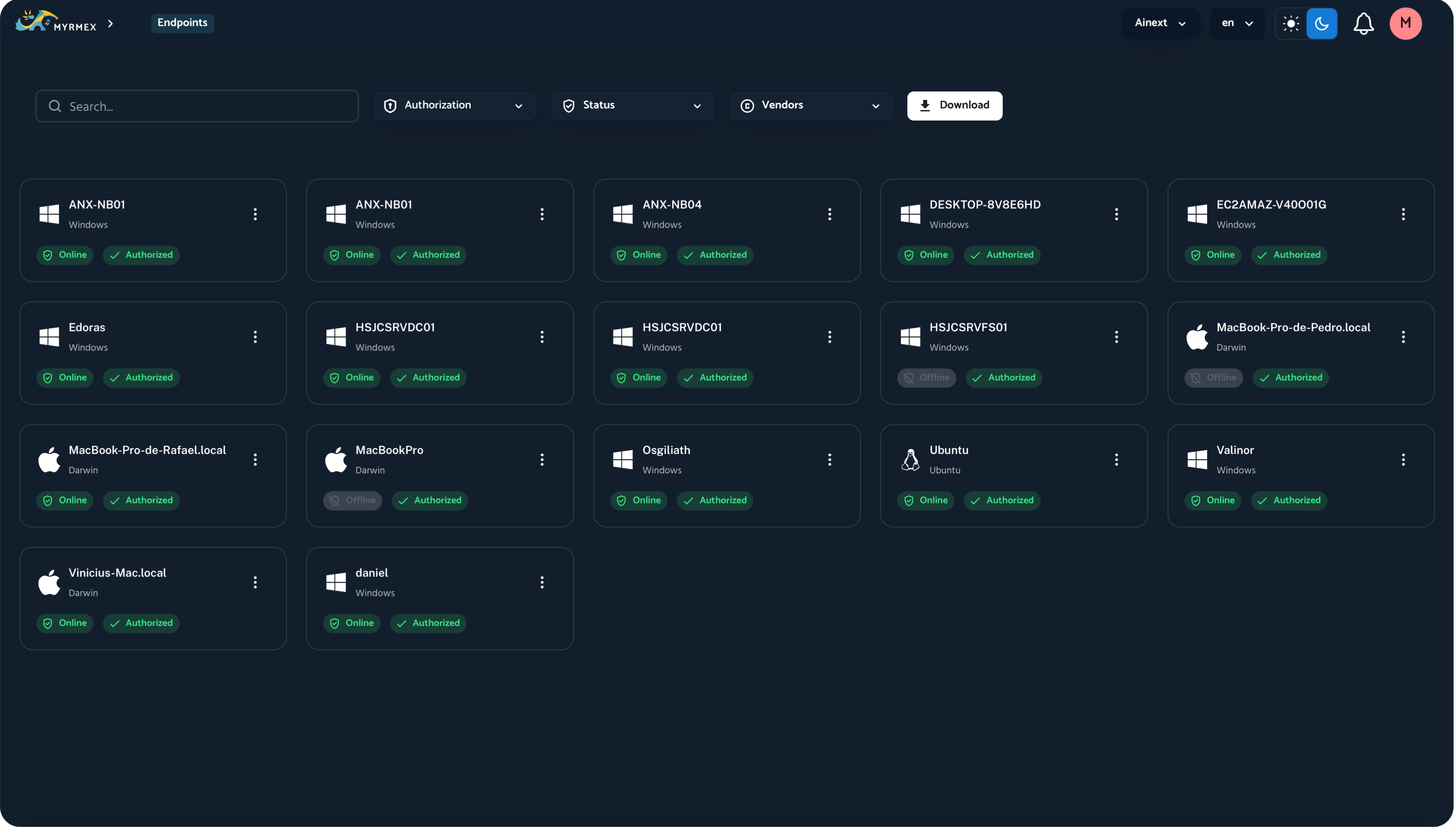
- Agents installed in the environment;
- Active integrations with other security systems or services. This area is essential for maintaining control and configuration of the components connected to Myrmex.
Log Management
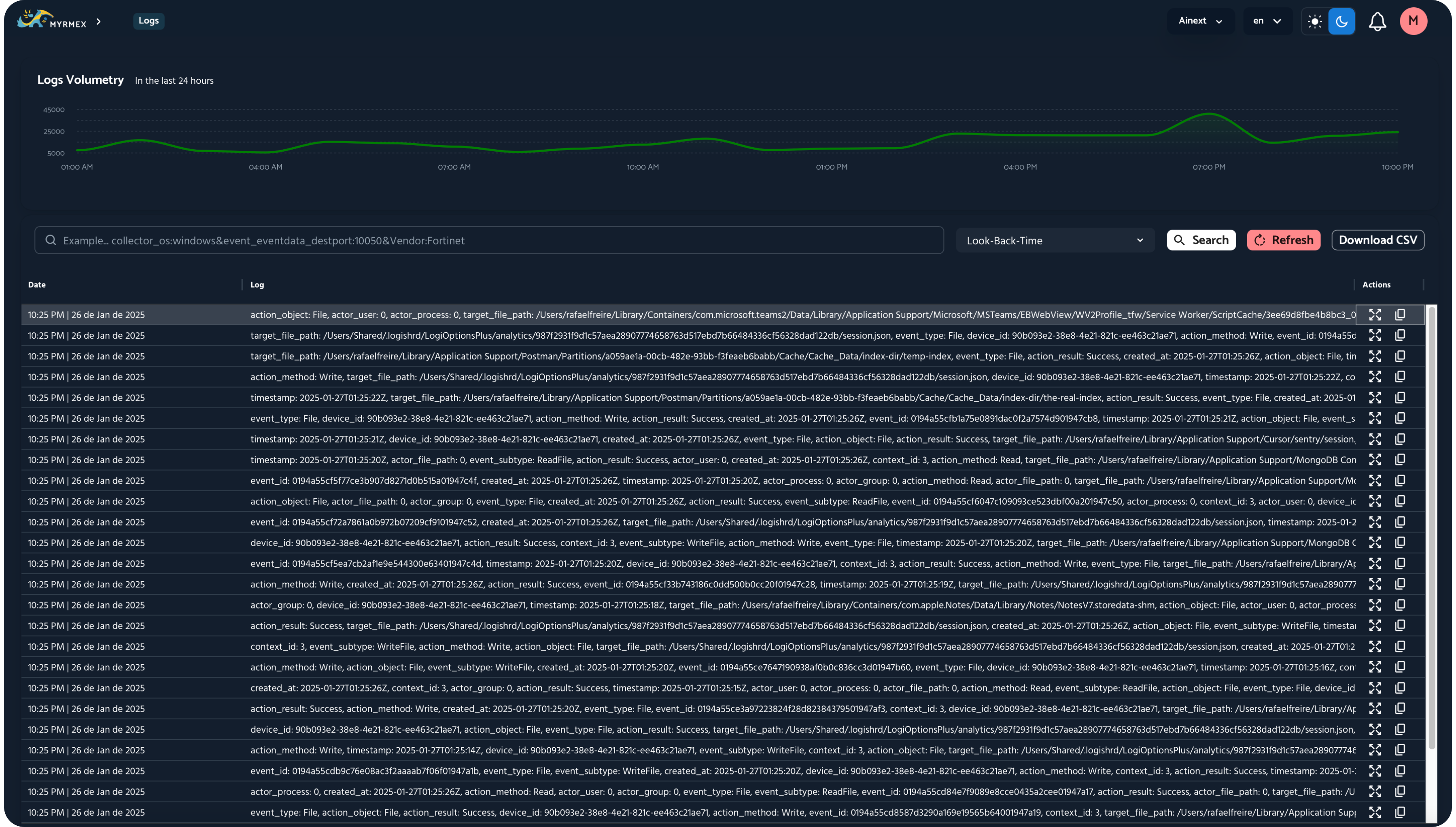
Alerts
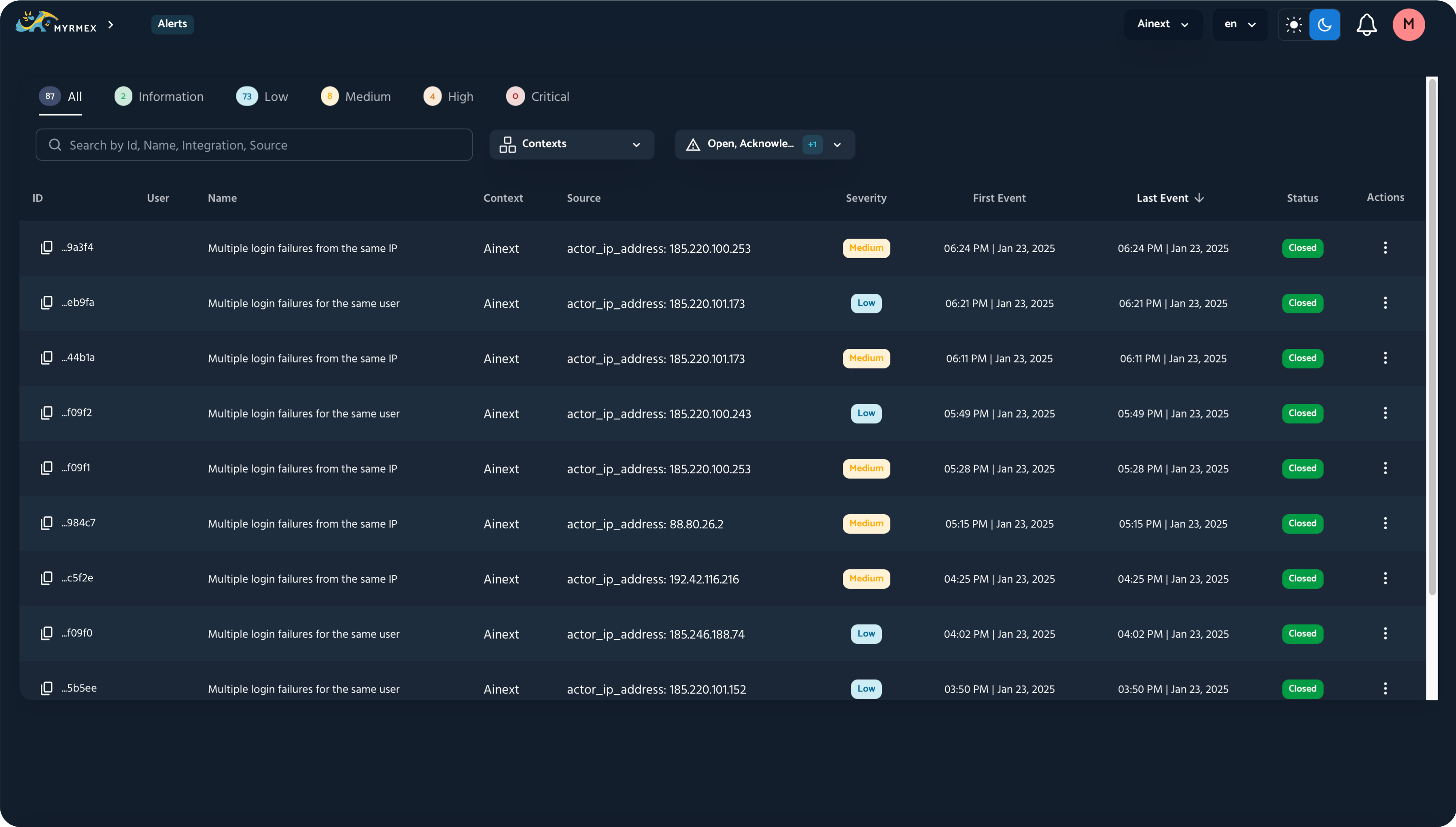
- Tactics used by the attacker;
- Threat details;
- The investigation carried out by MYRMEX AI, as well as its recommendations.
Alert Details
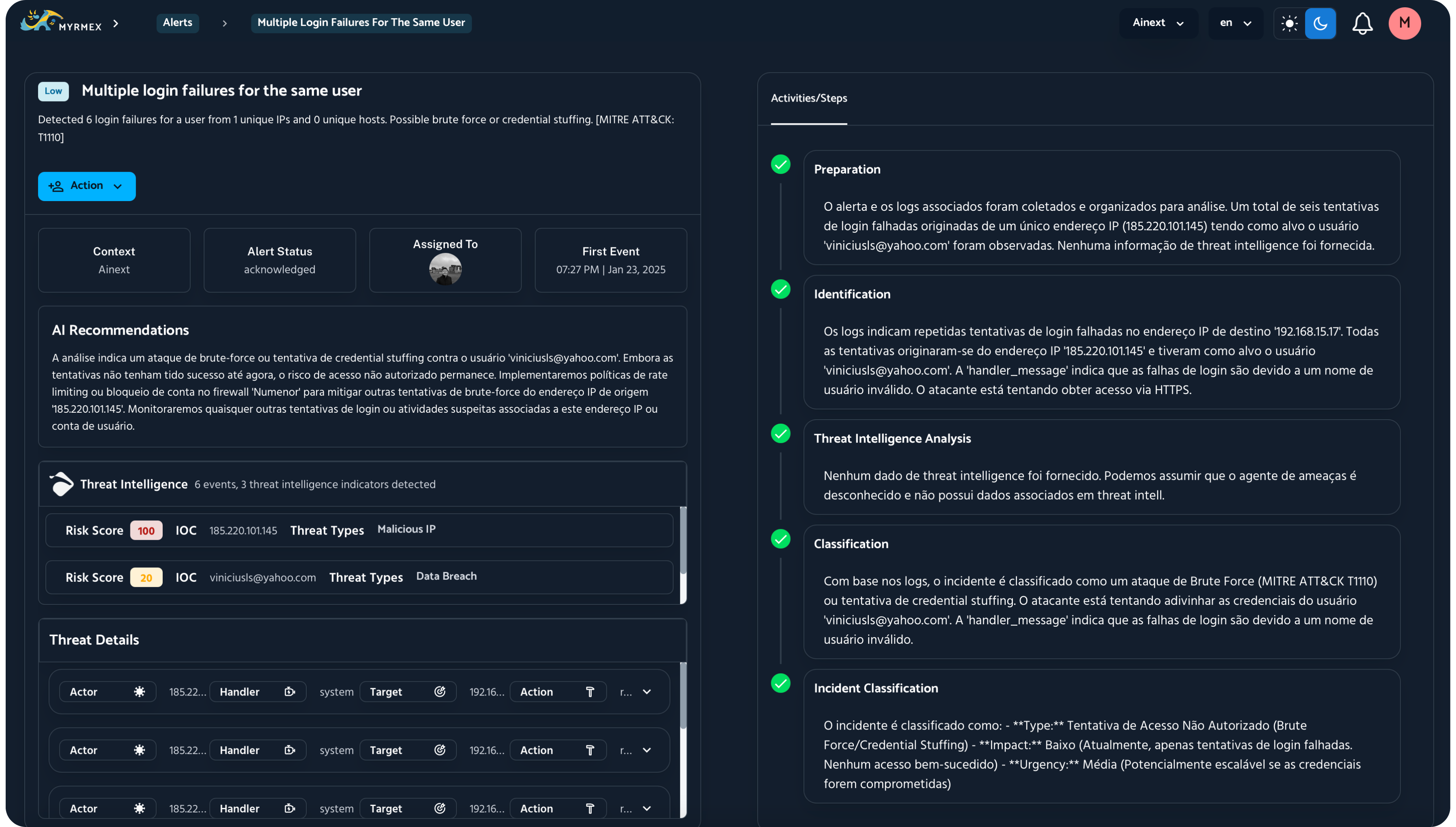
- Suspicious Activity Analysis: Identifies unauthorized access attempts, such as Brute Force and Credential Stuffing attacks.
- MITRE ATT&CK Integration: Classifies incidents based on recognized techniques (e.g., T1110).
- Automatic Log Analysis: Reviews authentication data, logs, and patterns to determine the source and impact of security events.

